Military-Grade Protection
Torzon implements cutting-edge cryptographic protocols designed to protect users against current and future threats. As of January 2026, Torzon has upgraded to NIST FIPS 205 (SLH-DSA) post-quantum signatures. Learn how to access Torzon safely with our complete guide.
Torzon completed migration to NIST-standardized post-quantum algorithms (FIPS 205 SLH-DSA) on January 15, 2026. All vendor verifications and critical communications now use quantum-resistant signatures. Additionally, DDoS mitigation capacity increased by 40% across all mirror infrastructure.
Post-Quantum Cryptography
Traditional encryption methods face an existential threat from quantum computers. Torzon has proactively implemented post-quantum cryptographic algorithms that remain secure even against attacks from future quantum systems.
Our implementation uses lattice-based cryptography for key exchange and digital signatures, ensuring that intercepted communications cannot be decrypted retroactively when quantum computers become practical.
This forward-thinking approach means your data remains protected not just today, but for decades to come. Torzon is among the first darknet markets to implement NIST-approved post-quantum algorithms. Explore all Torzon marketplace features built on this foundation.
What This Means For You
- Your encrypted messages remain private indefinitely
- Transaction records cannot be compromised by future technology
- Account credentials resist quantum brute-force attacks
- Future-proof security that evolves with threats
Quantum-Resistant
Lattice-based cryptography protects against both classical and quantum attacks. Your security is future-proof.
2-of-3 Multisig Escrow
Decentralized payment protection that eliminates single points of failure. No single party can steal funds or manipulate transactions.
Buyer Initiates
Payment sent to multisig address requiring 2-of-3 signatures
Vendor Ships
Order fulfilled and marked as shipped in system
Release or Dispute
Buyer confirms receipt or opens dispute for resolution
Key Holders
Any two parties can authorize fund release. This prevents both exit scams and buyer fraud while enabling fair dispute resolution. The market cannot access your funds without your consent. Get verified Torzon links to start using this secure system.
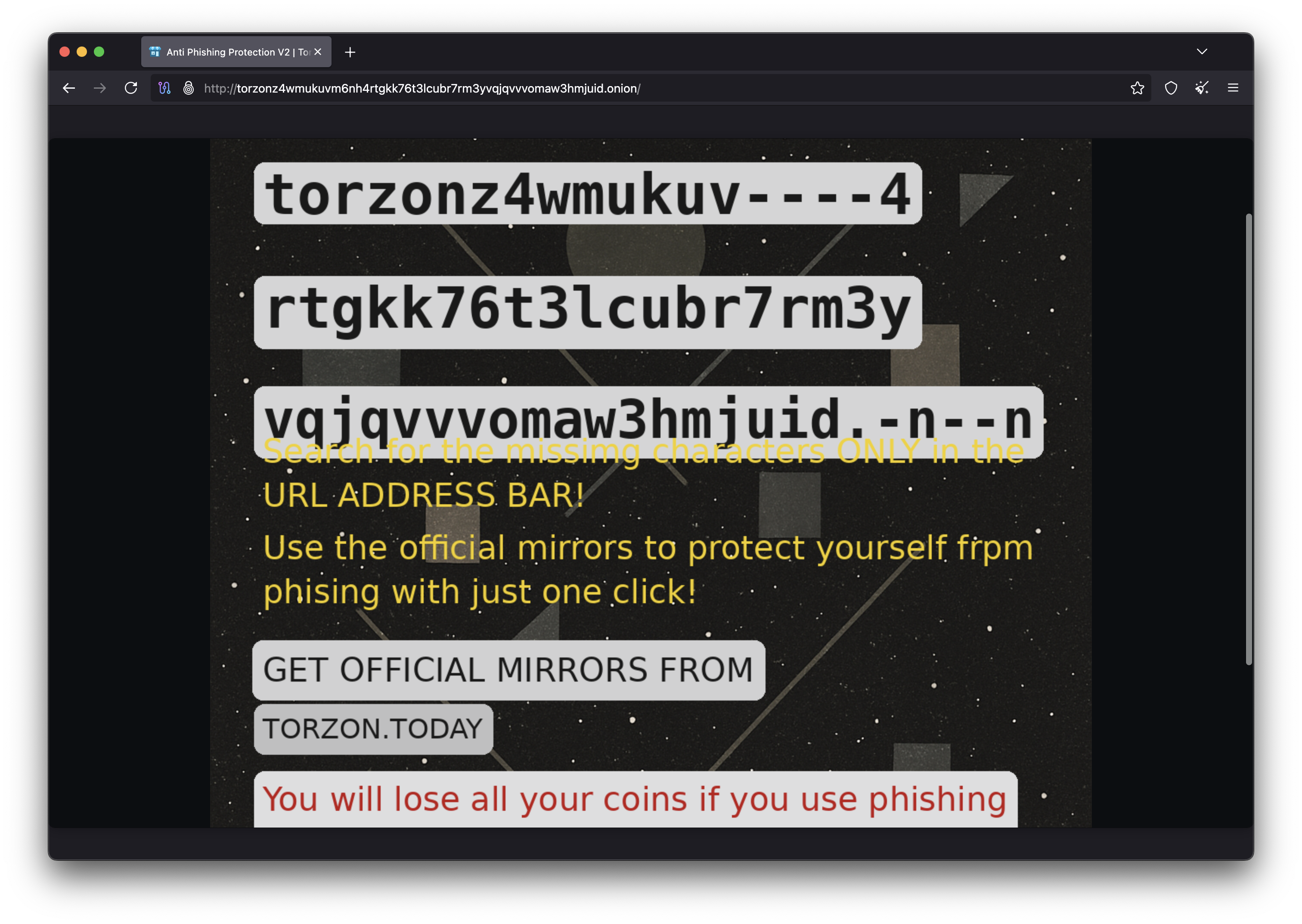
URL Verification
Anti-phishing challenge ensures you're on the real Torzon
Anti-Phishing Protection
Torzon displays a personal anti-phishing phrase on every login screen. This phrase is chosen by you during registration and known only to you and the authentic Torzon servers.
If you ever reach a login page that doesn't display your personal phrase, you're on a phishing site. Close it immediately and navigate to a verified link from our mirrors page.
This simple but effective measure has prevented countless credential theft attempts and remains one of the most important security features you can use. Follow our Torzon access guide to set up your anti-phishing phrase.
DDOS Protection & Captcha System
Torzon Market employs advanced DDOS protection to maintain 99.9% uptime even during coordinated attacks. The captcha verification system ensures only legitimate users can access the marketplace while blocking automated threats.
During high traffic periods or attacks, users may encounter a brief queue system that protects server resources and ensures fair access for all Torzon users.
These protection measures work seamlessly in the background, providing security without significantly impacting user experience. Return to the Torzon Market homepage to learn more.

DDOS Protection
Visual captcha prevents automated attacks
Understanding Torzon's Cryptographic Foundation
The cryptographic architecture underlying Torzon Market represents a significant advancement in darknet marketplace security. Unlike platforms that rely solely on traditional encryption methods, Torzon has implemented a hybrid cryptographic system that combines proven classical algorithms with next-generation post-quantum protocols. This dual approach ensures immediate security through battle-tested methods while providing future-proof protection against quantum computing threats.
The Quantum Computing Threat
Quantum computers leverage quantum mechanical phenomena to perform calculations that would be impossible for classical computers. While current quantum systems remain limited, rapid advances in the field suggest that cryptographically relevant quantum computers may emerge within the next decade. When this occurs, many encryption schemes currently considered secure will become vulnerable to quantum attacks capable of breaking them in hours rather than centuries.
The threat extends beyond future communications to historical data. Adversaries practicing "harvest now, decrypt later" strategies are already collecting encrypted communications for future decryption when quantum computers become available. This reality makes quantum-resistant encryption essential for protecting information that must remain confidential for extended periods. Torzon's early adoption of post-quantum cryptography addresses this timeline threat directly.
Lattice-Based Cryptography Explained
Torzon's post-quantum implementation relies on lattice-based cryptographic constructions, a family of algorithms whose security derives from the mathematical difficulty of certain problems involving geometric lattices in high-dimensional spaces. These problems, including the Shortest Vector Problem (SVP) and Learning With Errors (LWE), remain computationally intractable even for quantum computers, providing confidence in their long-term security.
The specific algorithms implemented on Torzon include CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures, both of which were selected by NIST (National Institute of Standards and Technology) after extensive analysis in their Post-Quantum Cryptography Standardization project. This selection provides external validation of the algorithms' security properties and resistance to known attack vectors.
Implementation Security Measures
Correct implementation of cryptographic algorithms is equally important as the algorithms themselves. Torzon's development team follows cryptographic best practices including constant-time implementations that resist timing side-channel attacks, secure random number generation using hardware entropy sources, and defense-in-depth approaches that maintain security even if individual components are compromised.
The platform undergoes regular security assessments by independent cryptographers who review both the algorithmic implementations and the broader security architecture. Findings from these audits are addressed promptly, with critical vulnerabilities patched within hours of discovery. This continuous security improvement process ensures that Torzon's cryptographic foundation remains robust as new attack techniques emerge. See our verified Torzon mirror links to access these protected systems.
How Multisig Escrow Protects Your Transactions
The 2-of-3 multisignature escrow system represents one of Torzon's most important innovations in marketplace security. Traditional escrow systems require users to trust a central entity to hold and release funds fairly. Multisig eliminates this trust requirement by distributing control among three independent parties, ensuring that no single actor can unilaterally access or manipulate transaction funds.
Technical Implementation
When a buyer initiates a purchase on Torzon, the system generates a unique Bitcoin address controlled by a 2-of-3 multisig script. This script specifies that releasing funds requires valid signatures from any two of three designated public keys: one controlled by the buyer, one by the vendor, and one by Torzon Market. The buyer's payment is sent to this address, where it remains secured by the multisig requirement until the transaction concludes.
The multisig address is generated deterministically using the public keys of all three parties, meaning anyone can verify that the address was created correctly. This transparency allows users to audit the escrow process and confirm that funds are genuinely secured by the specified key combination rather than controlled solely by the marketplace.
Standard Transaction Flow
In successful transactions, the release process is straightforward. After receiving their order and confirming satisfaction, buyers finalize the order through the Torzon interface. This action triggers the buyer's signature on a release transaction sending funds to the vendor's address. The marketplace automatically adds its signature, meeting the 2-of-3 requirement and broadcasting the release transaction to the Bitcoin network.
This flow means vendors receive payment only after buyers confirm receipt, protecting against vendors who ship empty packages or wrong items. Simultaneously, once an order is finalized, vendors receive their payment regardless of any subsequent buyer claims, protecting against buyers who falsely claim non-delivery to obtain refunds while keeping products.
Dispute Resolution Process
When disagreements arise, either party can initiate a dispute that places the transaction in a pending state. Torzon's moderator team then investigates the situation, reviewing all available evidence including order details, communication logs, shipping tracking information, and any documentation provided by both parties. Moderators make decisions based on established policies and the preponderance of evidence.
Following investigation, moderators provide their signature either on a release transaction to the vendor (if the vendor fulfilled their obligations) or a refund transaction to the buyer (if the vendor failed to deliver as promised). This signature, combined with one of the party signatures, meets the 2-of-3 requirement and resolves the dispute. The losing party can appeal through Torzon's escalation process if they believe the decision was incorrect.
Protection Against Exit Scams
Multisig escrow provides critical protection against exit scams, a major risk on darknet marketplaces. In traditional custodial escrow systems, marketplaces hold funds directly and can simply disappear with accumulated balances. With multisig, Torzon never has unilateral access to user funds. Even if the marketplace ceased operations, funds in escrow would not be lost - buyers and vendors holding two of three keys could still release funds through direct coordination.
Account Security Best Practices
While Torzon provides robust platform-level security, individual account security depends significantly on user behavior. Following established security best practices dramatically reduces the risk of account compromise, fund theft, and identity exposure. These recommendations represent the collective wisdom of experienced darknet marketplace users and security professionals.
Strong Authentication Setup
Your Torzon password should be unique to this platform, never reused from any other account anywhere. Use a password of at least 16 characters combining uppercase letters, lowercase letters, numbers, and special characters. Consider using a password manager (running locally, not cloud-based) to generate and store complex passwords securely. Never write passwords down or store them in unencrypted files.
Enable two-factor authentication immediately after account creation. PGP-based 2FA provides the strongest protection, requiring you to decrypt a challenge message using your private key to complete login. This ensures that even if an attacker obtains your password, they cannot access your account without also possessing your PGP private key - an extremely unlikely combination.
PGP Key Management
Your PGP key pair forms the foundation of secure communication and advanced authentication on Torzon. Generate keys with at least 4096 bits for RSA or use modern elliptic curve options for equivalent security with smaller key sizes. Your private key should be stored only on encrypted storage with a strong passphrase - never on cloud services or internet-connected devices beyond what's necessary for marketplace use.
Upload your public key to your Torzon profile to enable encrypted communication. All messages from vendors and marketplace staff will be encrypted using this key, ensuring that only you can read them. Verify that vendors' public keys match those published on their profiles before encrypting sensitive information like shipping addresses.
Operational Security Fundamentals
Always access Torzon exclusively through Tor Browser, never through regular browsers or Tor proxies. Keep Tor Browser updated to the latest version to ensure you have current security patches. Consider using Tails or Whonix operating systems for additional isolation between your marketplace activity and your regular computing environment.
Verify your anti-phishing phrase every single time before entering login credentials. This five-second check has prevented countless account compromises and should become automatic habit. If you ever see an incorrect phrase or no phrase at all, close the page immediately without entering any information and navigate to Torzon using a verified link from your bookmarks.
Additional Security Layers
Multiple overlapping security measures ensure comprehensive protection at every level.
2FA Authentication
Optional two-factor authentication using PGP or TOTP adds another layer of protection to your account login process.
PGP Encryption
All sensitive communications encrypted with your public key. Only you can read messages sent to your account.
Auto-Encrypt
Messages automatically encrypted using vendor PGP keys. No manual steps required for secure communication.
Session Timeout
Automatic logout after period of inactivity protects against unauthorized access if you leave your device.
JavaScript-Free
Core functionality works without JavaScript enabled, reducing attack surface and improving privacy.
Login History
View all recent login attempts and active sessions. Immediately detect unauthorized access attempts.
Secure Authentication Process
Every Torzon login is protected by multiple security checkpoints.
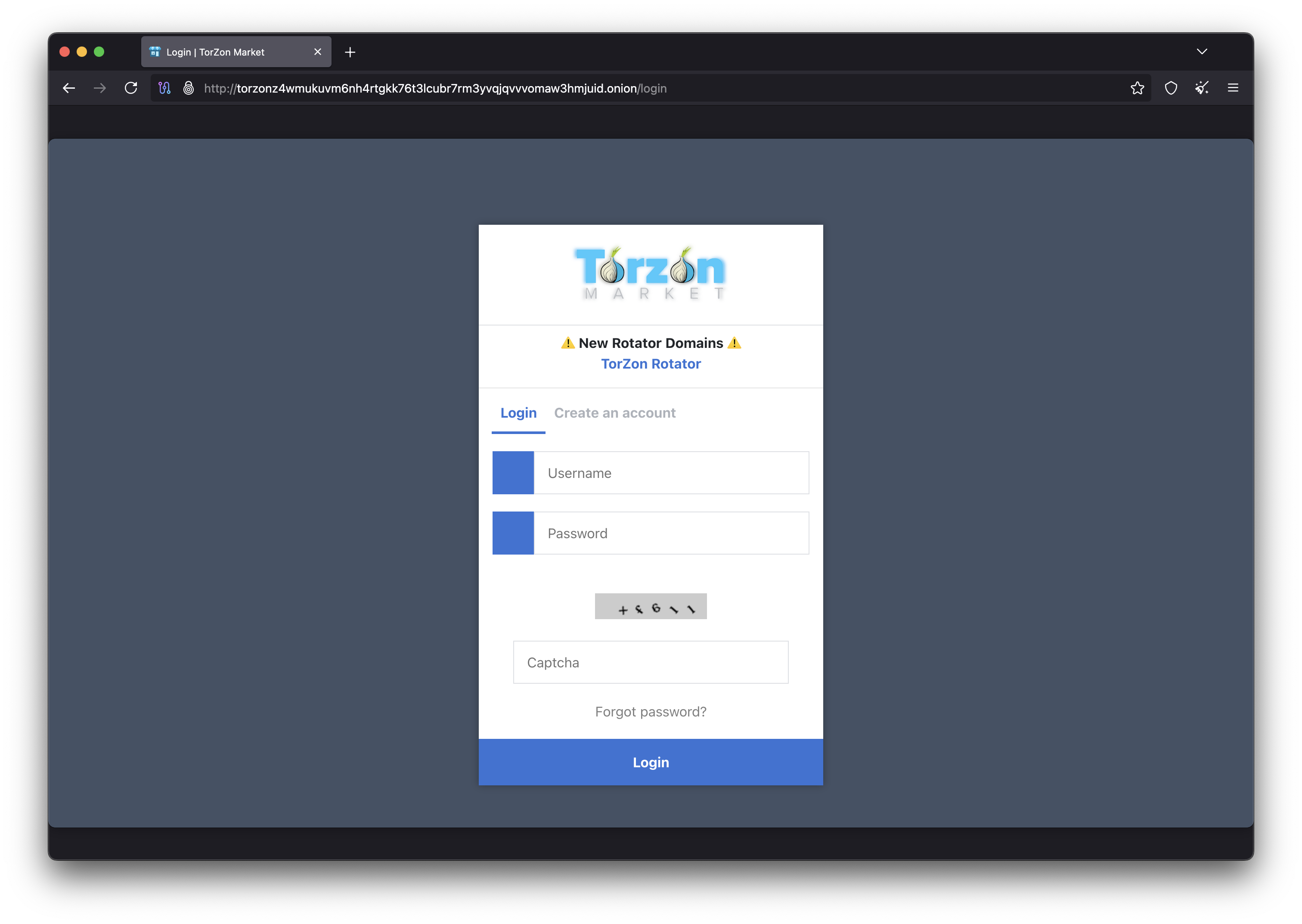
Secure Login Portal
Multi-layer authentication with captcha verification
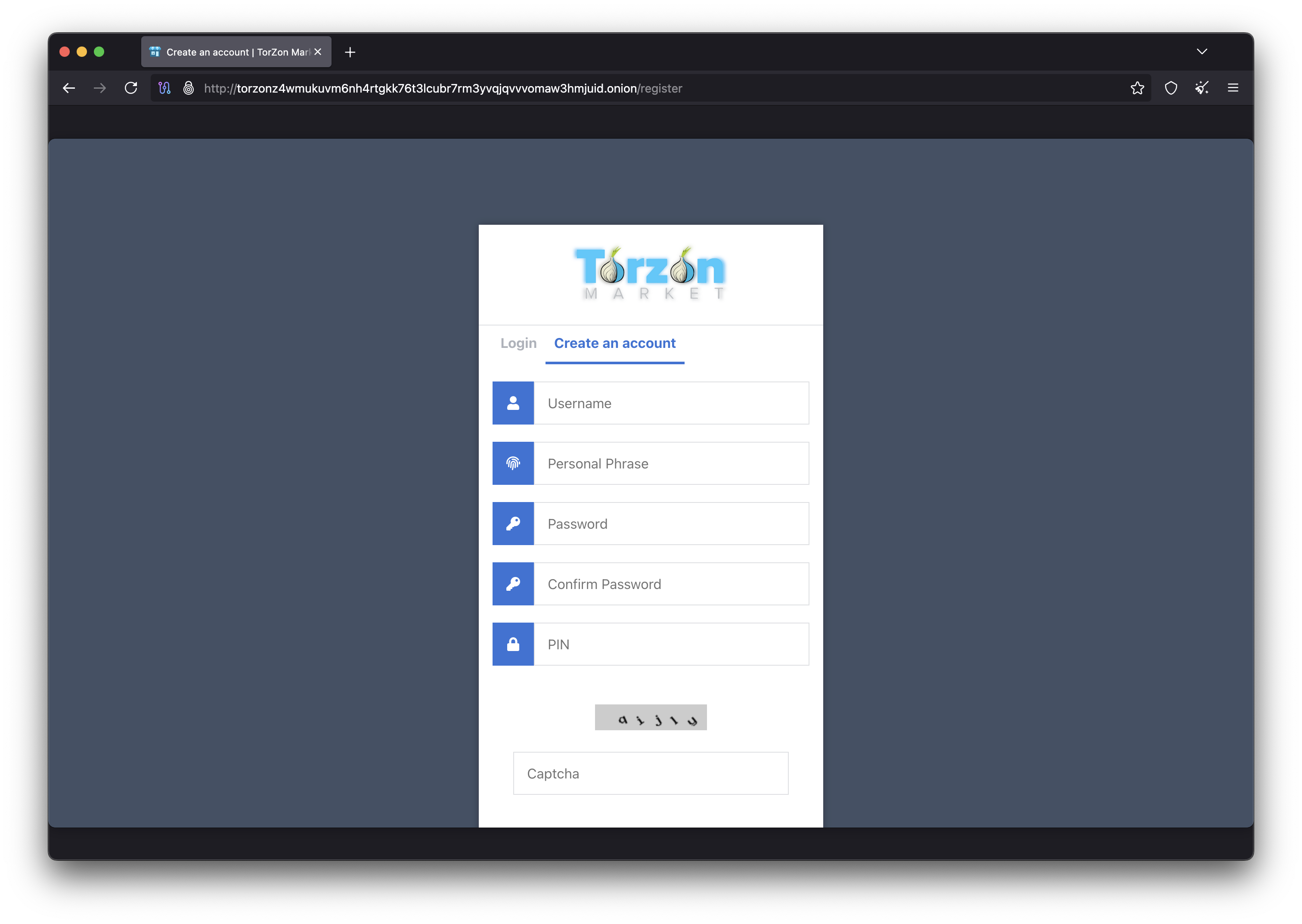
Security-First Registration
Set up anti-phishing phrase, PIN, and strong password
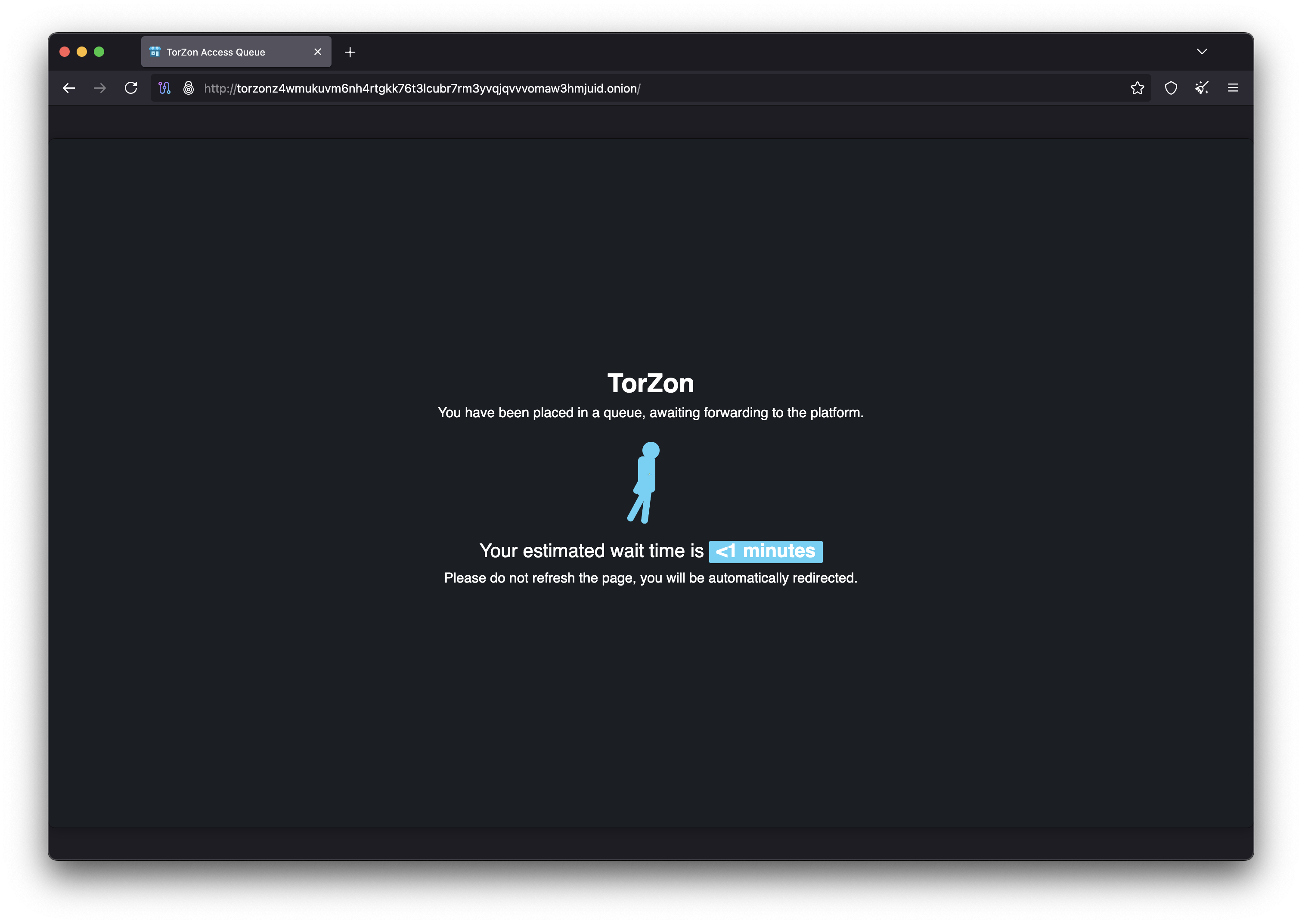
Queue system protects during high traffic
Torzon Market Security - Complete Protection Guide
Torzon security is the foundation of the Torzon Market experience. The Torzon marketplace implements multiple layers of Torzon protection to safeguard every Torzon user. When you access Torzon through verified Torzon links, you benefit from the most advanced Torzon security infrastructure in the darknet market ecosystem. Torzon Market prioritizes Torzon user safety above all else.
The Torzon encryption system uses post-quantum cryptography to protect all Torzon communications and Torzon transactions. Every Torzon message is encrypted, every Torzon payment is secured through Torzon multisig, and every Torzon account is protected by Torzon's advanced authentication. Torzon Market continues to upgrade Torzon security measures to stay ahead of emerging threats to Torzon users.
Understanding Torzon security features is essential for safe Torzon Market usage. The Torzon anti-phishing system protects Torzon users from fake Torzon sites. Torzon 2FA adds extra Torzon account protection. The Torzon PGP system enables encrypted Torzon messaging. Together, these Torzon security layers create comprehensive Torzon protection that makes Torzon Market the safest darknet marketplace available.
Access Torzon Market safely by following Torzon security best practices. Use only verified Torzon links from our Torzon mirror page. Enable Torzon 2FA on your Torzon account. Verify your Torzon anti-phishing phrase before every Torzon login. With proper Torzon security habits, your Torzon Market experience will be both safe and secure. Torzon is committed to Torzon user protection.
Torzon Market Security - Frequently Asked Questions
Expert answers about Torzon Market security, Torzon encryption, Torzon authentication, and Torzon protection measures. Learn how Torzon keeps your marketplace activities secure and private.
What is Post-Quantum Cryptography and Why Does Torzon Use It?
Torzon Market implements post-quantum cryptography to future-proof security against emerging quantum computing threats. Traditional encryption methods protecting current darknet marketplaces will become vulnerable when quantum computers reach sufficient power - Torzon has proactively implemented quantum-resistant algorithms. The Torzon cryptographic infrastructure uses lattice-based encryption schemes that remain secure even against quantum attacks. This forward-thinking Torzon security approach ensures that Torzon communications intercepted today cannot be decrypted in the future using quantum computers. Torzon Market is among the first darknet marketplaces implementing post-quantum protection, demonstrating Torzon's commitment to long-term user security. The Torzon development team collaborated with cryptography researchers to implement proven quantum-resistant algorithms. While other marketplaces will scramble to upgrade when quantum threats materialize, Torzon users are already protected. The Torzon post-quantum implementation adds minimal performance overhead while providing maximum future security. This proactive Torzon security measure exemplifies how Torzon prioritizes user protection over short-term convenience.
How Does Torzon's 2-of-3 Multisig Escrow Prevent Exit Scams?
Torzon Market's multisignature escrow system represents a fundamental security innovation preventing exit scams that have destroyed other marketplaces. Traditional escrow gives marketplaces complete control over funds - Torzon uses cryptographic multisig where funds require two of three signatures: buyer, vendor, and Torzon moderators. When you purchase on Torzon, cryptocurrency is locked in a special Bitcoin address that mathematically requires two parties to cooperate for fund release. The Torzon vendor cannot take funds without buyer consent, buyers cannot refund without vendor agreement, and Torzon Market cannot unilaterally steal funds. This Torzon escrow architecture makes exit scams mathematically impossible - Torzon administrators lack the cryptographic keys needed to steal escrowed funds alone. The Torzon multisig system uses standard Bitcoin protocols, making the security provable and verifiable. Transparent Torzon blockchain transactions demonstrate that multisig addresses actually hold user funds rather than marketplace wallets. This Torzon innovation has influenced other marketplaces to implement similar protections, but Torzon's implementation remains most mature and battle-tested through years of operation.
What is Torzon Anti-Phishing Protection and How Does It Work?
Torzon Market's anti-phishing system protects users from credential theft via fake login pages impersonating Torzon. When registering, Torzon users create personal anti-phishing phrases displayed prominently on authentic Torzon login pages. These Torzon phrases are unique to each account and stored encrypted on Torzon servers. Phishing sites cannot display your correct Torzon anti-phishing phrase because they don't possess the cryptographic keys to decrypt it. Before entering credentials on any Torzon login page, users verify their personal phrase appears correctly - if missing or incorrect, the site is fake. This Torzon security feature has prevented countless account compromises by alerting users before credentials are entered on phishing sites. The Torzon anti-phishing system is foolproof: legitimate Torzon sites always display your phrase, fake sites never can. Torzon also implements URL verification reminders encouraging users to bookmark official Torzon mirror links rather than searching for Torzon via potentially compromised search engines. Combined with PGP-signed Torzon canary messages, users have multiple methods to verify they're accessing authentic Torzon Market rather than phishing imposters.
How Does Torzon's RAM-Only Architecture Enhance Security?
Torzon Market operates on RAM-only servers that never write data to persistent storage, drastically reducing law enforcement seizure risks. Traditional servers store data on hard drives that persist after power loss - seized servers provide complete databases to authorities. Torzon's infrastructure runs entirely in RAM, meaning all data vanishes instantly if servers lose power or are seized. The Torzon database exists only in volatile memory, with regular encrypted backups stored in undisclosed distributed locations. If law enforcement seizes Torzon servers, they recover only blank hardware without user data, transaction records, or private messages. This Torzon architecture has been proven effective during previous darknet marketplace seizures where RAM-only systems yielded no usable evidence. The Torzon platform automatically implements emergency data wipes if unauthorized physical access is detected. While this Torzon security measure doesn't prevent operation disruption, it protects user privacy by ensuring seized hardware contains no compromising data. Regular Torzon users benefit from knowing their marketplace activities leave minimal forensic traces. The Torzon RAM-only design represents best practices for darknet marketplace security architecture.
What Makes Torzon's 2FA Implementation More Secure Than Others?
Torzon Market implements comprehensive two-factor authentication that significantly exceeds typical marketplace 2FA. The Torzon 2FA system supports multiple methods: TOTP authenticator apps (Google Authenticator, Authy), PGP-signed challenge responses, and account-specific security questions. Unlike marketplaces offering only basic TOTP, Torzon allows users to configure backup 2FA methods preventing lockouts if primary devices are lost. The Torzon 2FA implementation requires codes for sensitive operations beyond just login: withdrawals, message decryption keys, and account setting changes all require Torzon 2FA verification. Users can configure different Torzon 2FA methods for different operations, balancing security and convenience according to personal threat models. The Torzon platform never stores 2FA seeds on servers - codes are generated client-side and verified cryptographically. This Torzon approach prevents server compromises from exposing 2FA secrets. Torzon also implements rate limiting on 2FA attempts, preventing brute force attacks against authentication codes. The Torzon 2FA system logs all verification attempts with IP addresses and timestamps, enabling users to detect unauthorized access attempts. Comprehensive Torzon 2FA documentation guides users through setup and backup procedures.
How Does Torzon PGP Encryption Protect User Communications?
Torzon Market's PGP integration provides end-to-end encryption for sensitive communications that remain secure even if Torzon servers are completely compromised. PGP (Pretty Good Privacy) uses public-key cryptography where each Torzon user generates a key pair: public keys encrypt messages, private keys decrypt them. Torzon users upload public PGP keys to their profiles, enabling other Torzon users and vendors to send encrypted messages. When composing Torzon messages containing sensitive information like shipping addresses, the Torzon interface automatically encrypts content with recipient's public key before transmission. The encrypted Torzon message transits and stores on Torzon servers as unreadable ciphertext - only the intended recipient possessing the corresponding private key can decrypt it. This Torzon encryption architecture means compromised servers yield no useful plaintext even if every message is seized. The Torzon PGP system encourages users to generate keys on secure offline computers, with private keys never touching Torzon infrastructure. Torzon vendors particularly benefit from PGP encryption, protecting customer addresses even during seizures. The Torzon platform provides tutorials for PGP setup and key management aimed at non-technical users. Modern Torzon encryption represents industry best practices for marketplace communication security.
What Security Auditing Does Torzon Perform?
Torzon Market undergoes regular security audits by independent researchers evaluating the Torzon codebase, infrastructure, and operational practices. The Torzon security team maintains an active bug bounty program rewarding researchers who identify and responsibly disclose Torzon vulnerabilities. Discovered security issues receive immediate Torzon attention with patches deployed typically within 48 hours. The Torzon audit program covers multiple domains: application security (XSS, SQL injection, authentication bypasses), cryptographic implementation correctness, server hardening and network security, payment system integrity, and anti-fraud measures. Torzon publishes regular security bulletins describing addressed vulnerabilities without exposing exploitation details while issues remain unpatched. This transparent Torzon security approach builds user trust by demonstrating proactive vulnerability management. The Torzon infrastructure uses standard security practices: regular software updates, minimal attack surface, defense-in-depth architectures, and continuous monitoring for suspicious activities. Torzon administrators undergo operational security training covering proper key management, secure communications, and threat awareness. The Torzon security program learns from failures at other marketplaces, implementing preventive measures before similar attacks target Torzon. Ongoing security investment distinguishes Torzon from marketplaces treating security as an afterthought.
How Does Torzon Protect Against DDoS Attacks?
Torzon Market maintains exceptional uptime through comprehensive DDoS mitigation that keeps Torzon accessible during attacks affecting other marketplaces. The Torzon infrastructure distributes across multiple hosting providers and jurisdictions, preventing single points of failure. Tor hidden services inherently provide some DDoS protection by obscuring server locations, but Torzon implements additional layers. The Torzon platform uses proof-of-work captchas during high-traffic periods, requiring computational effort that makes mass automated requests expensive for attackers. Legitimate Torzon users solve captchas once and receive session tokens valid for extended periods. Sophisticated Torzon rate limiting identifies and blocks abusive traffic patterns while allowing normal user behavior. The Torzon mirror network provides redundancy - if one mirror suffers attacks, users seamlessly access alternative Torzon mirrors. The Torzon team coordinates with Tor Project developers to implement cutting-edge onion service DDoS protections as they become available. Queue systems throttle traffic during overwhelming demand, preserving Torzon functionality rather than allowing complete service failure. Monitoring systems alert Torzon administrators immediately when attacks begin, enabling rapid response. The Torzon uptime record (99.9%+) demonstrates effectiveness of these multi-layered protections against sustained DDoS campaigns.
Security Video Guides
Deepen your understanding of encryption, quantum computing threats, and modern cybersecurity practices.
End-to-End Encryption Explained
AES Encryption Deep Dive
Quantum Computing & Encryption
Ready to Experience Secure Torzon Trading?
Access Torzon Market with verified Torzon links and follow our Torzon security guide for maximum Torzon protection.